How is Hyve secured by Symbiotic?
In the early days of Hyve’s development, a strategic decision was made to utilize Symbiotic for security. Besides an experienced and motivated team, Symbiotic’s Staking and customizable slashing mechanisms offer a security model that scales.
Jul 24, 2025
In the early days of Hyve’s development, a strategic decision was made to utilize Symbiotic for security. Besides an experienced and motivated team, Symbiotic’s Universal Staking and customizable slashing mechanisms offer a security model that scales alongside the protocols it protects. Gone are the days of bootstrapping your own validator set, or relying on whatever limited security is available on a fast, up-and-coming chain. So, how does this actually work? Let’s use Hyve as an example.
Vaults, Restakers, and Operators
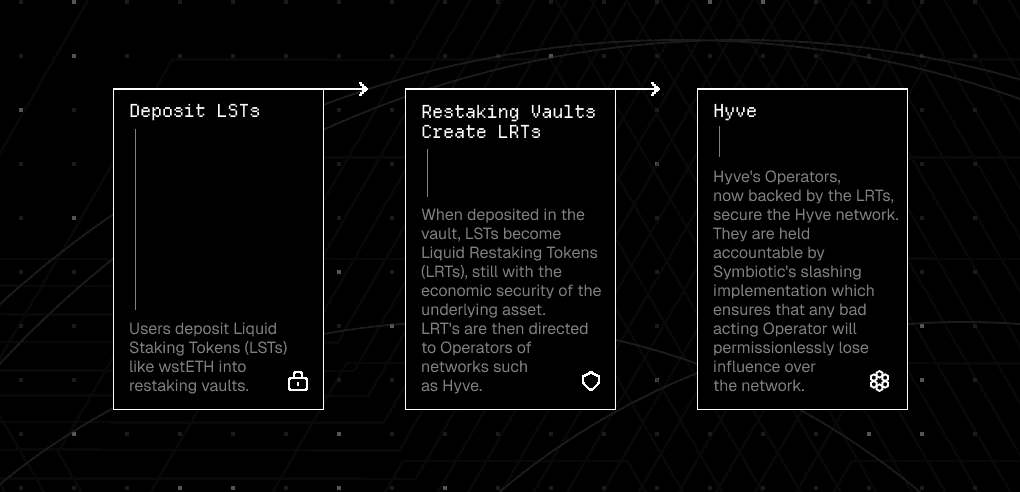
First, let’s define staking vaults.
Symbiotic provides non-custodial smart contracts that hold user assets, called staking vaults. These vaults contain the "restaked" assets that provide economic security to all and any networks.
A project like Hyve creates its own vault on Symbiotic with the help of curators. Besides deploying the vault, curators define key parameters such as:
What kind of collateral is accepted
Risk settings (e.g., slashing conditions, liquidation thresholds)
Operator eligibility criteria (who can participate in that vault)
Now that we’ve defined vault and curators, how about restakers?
Anyone who wants to help secure Hyve can deposit (restake) approved assets into this vault, putting their capital to work in exchange for rewards.
Now, operators: the infrastructure providers doing the actual protocol work for secured networks. Operators can be data availability nodes, proof networks, or other job-specific actors. Economic weight (collateral) is delegated to Operators by the Curator, empowering them to act on Hyve’s behalf.
While operators and restakers share the potential risk and the potential upside of native network rewards, curators set a fee structure based on assets deposited or vault performance.
Slashing
The main risk faced by operators and restakers is slashing. Slashing means the Operator is penalized, their delegated stake can be burned, reduced, or reallocated. This reduces their influence over the network as well as their potential rewards, creating a strong incentive for them to perform their duties honestly and reliably.
Why Universal Staking Matters
Symbiotic also introduces Universal Staking, which expands the security model beyond ETH. Vaults can be configured to accept any asset the protocol chooses, including native tokens or LRTs. That means a project like Hyve can secure itself with any meaningful asset, even one that’s unrelated to the chain it's running on.
This removes the need to raise capital or build out a custom security model from scratch. It also enables cross-ecosystem security, where value from one ecosystem helps secure another.
What This Means for Hyve
Thanks to Symbiotic, Hyve doesn’t need to reinvent the wheel when it comes to network security. Instead of spending months recruiting validators or cobbling together incentives, we can plug directly into a modular, scalable security framework, while still customizing slashing logic, operator roles, and accepted assets to fit our unique needs.
That means we stay lean, move fast, and focus on delivering value, with the confidence that Symbiotic has our back.
Disclaimer:
This content is provided for informational and educational purposes only and does not constitute legal, business, investment, financial, or tax advice. You should consult your own advisers regarding those matters.
References to any protocols, projects, or digital assets are for illustrative purposes only and do not represent any recommendation or offer to buy, sell, or participate in any activity involving digital assets or financial products. This material should not be relied upon as the basis for any investment or network participation decision.
Hyve and its contributors make no representations or warranties, express or implied, regarding the accuracy, completeness, or reliability of the information provided. Digital assets and decentralized networks operate within evolving legal and regulatory environments; such risks are not addressed in this content.
All views and opinions expressed are those of the authors as of the date of publication and are subject to change without notice.